
Curiously, the day I thought of her, she also thought of me. Why is love a bit strange? Why do even far away, a couple can still feel? Could it be a quantum effect? Perhaps entanglement …
Curiously, the day I thought of her, she also thought of me. Why is love a bit strange? Why do even far away, a couple can still feel? Could it be a quantum effect? Perhaps entanglement …
In this article I will share with you an episode of my life that allowed me to easily understand the concept of quantum entanglement. Moreover, I will explore the possible connection that it may have in the future with the end of cybersecurity. A summary of this article with some extra info appears in the following video:
Prague - On a winter day I arrived in Prague. I had no concrete plans, except to wait until the next day and take the plane to Moscow. What is the probability of meeting someone in a remote place, in a place you didn't even think you'd be? zero? Most people will say yes! But to me, with all the odds against me, I saw her after a long time in the city where Hitler had planned to live, did you know that? Hitler never destroyed Prague, he was delighted and wanted to keep it for him. In that same city, on a winter day, I saw her again, and understood that events, no matter how impossible they seem, can actually exist. Indeed! That is what quantum physics is about.
If I saw her, it was thanks to the flow of information, that today constantly moves around the world and most of the time we forget that it is there. It was in the 70's that a young student founded Microsoft to create a world where everybody could store its information. He did it! But over the years he was wrong. When the internet emerged, people sought to spread the information, they did so on a large scale and only two guys realized that this information should be efficiently selected. They founded Google in the 90's and succeeded with the plan, but over the years they were also wrong. People not only spread the information, they sought to interact because, after all, we like to socialize. A student saw an opportunity and consolidated a social network in 2003; however, over time, Facebook was also wrong. The world was changing at high speed and the cell phone became the loving gadget, the companies of that time did not see the potential of this device, except for one that in 2009 launched with his friends an instant messaging app called WhatsApp. There is no secret in saying that in a few years WhatsApp will also be wrong. What will come? You may already have the answer. Yes...! It is hidden in the flow of information. Microsoft kept it, Google selected it, Facebook shared it, and WhatsApp, among other apps, diversified it. It was, in fact, a WhatsApp message that allowed me to see her again. I was in transit to Moscow, I didn't know what I was going to do.
"Hello, are you in Prague...? I have been notified."
The message appeared on the screen of my cell phone. It was her! We said goodbye 6 months ago in Munich, near the Bürgerbräukeller where Hitler started his revolution. I went to Peru and never heard from her again. So how could she have been notified? The only thing I did when I got to Prague was to access Airbnb and check out a couple of apartments. They never responded. With the hours I understood that they actually did, I had registered a year ago with her number and I never changed it, that's why they contacted her. I had forgotten that detail, like many others that we are forgetting on the web... But what is interesting is that on that day, with all the odds against me, she just had arrived in Prague.
-Come with me tomorrow, I'm going to Avast -she told me that night while eating Trdelník in the old town. She had arrived for a work event. I had to choose between going to Moscow or staying in Prague.

If Bill Gates founded Microsoft in the 1970s and Larry Page and Sergey Brin founded Google in the 1990s, what happened in the 1980s? Prague has the answer, two Czechoslovaks created Avast. In the rudimentary equipment of that time, they programmed an antivirus without knowing that this would make them the founders of a cybersecurity company. When I visited the facilities I thought about it: "If Microsoft stored it... Avast secured it." However, I cannot say that Avast was wrong over time, on the contrary, cybersecurity is today one of the most important issues in the flow of information. Ransomwares, trojans, spywares, spams, worms, bots are just a few names that hackers use to alter or steal digital information. The funny thing is that these names have been increasing over time because everything is migrating to the web, to the point that today the most prominent attacks are those focused on mining cryptocurrencies. Yes! Even coins are already moving to the web. But we are just starting because what's next is the age of IoT (Internet of Things)...

IoT is what will come. All devices, from a toaster to a fan, will be connected through the internet, the information will be present at all times moving constantly around the world, this implies more hackers and therefore a greater need to secure the cyberspace. Indeed! Avast won the lottery, like Kaspersky, McAfee, Norton, and many others. Because if attacks are numerous today, what can we expect in the age of IoT? In Fig. 2 I present a map where each trace represents a cyber-attack in real time. I took it in Avast, in its operations center. But since every company over time is meant to fail, it is feasible to assume that Avast will do so too. "But how?" I questioned myself as I left the building walking in the direction of Na Pankráci. I found the answer arriving at the station. When I took my wallet out of my pants, two coins fell onto the ground, and when I observed them lying there, one was heads (H) and the other tails (T), so I thought: how many times can this occur? There are only four options, either they both come up heads (HH), or both come up tails (TT), or both come up with opposite values (HT or TH), therefore the probability is 2/4. What if it would be 4/4? That is, what would happen if we achieve that these coins would always fall with opposite values? Although it sounds strange... if this is the case, Avast would cease to exist, but even more strange is that we can achieve this.
To do so, let's imagine first a two-dimensional world, a fictional world where everything moves on the plane. Let's draw on it two computers distanced from each other and place the two coins on one of them. Being on the plane it is obvious that the coins can only take one value. Let's consider that one coin is heads and the other is tails. Does it look familiar to you? They just represent the bits of information: 1 (face) and 0 (tail). Let's imagine that Alice (A) wants to send some information to Bob (B), for this she will use her computer. For simplicity, she only sends one coin. Remember that it is a two-dimensional system, therefore the coin must travel on the plane until it reaches B. At an intermediate point it is feasible to assume that someone will be able to steal the information. For this you can imagine yourself leaving the bank with a certain amount of money and heading home. On your way home, a thief can still your money. These thieves in the computer world are called hackers and to avoid the assault it is convenient to have a cybersecurity software installed, which behaves like a police in your hometown. In Fig. 3 we represent this scenario.
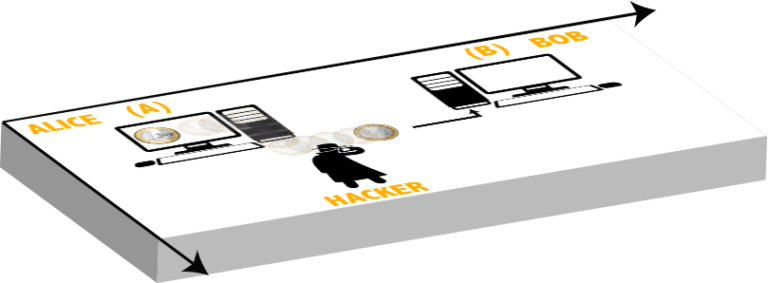
Let us now suppose that the hacker is not present, that is, let us assume that he does not exist. In this case, Bob will receive the coin and only Bob and Alice will be aware of the information. When Bob checks his coin, he will immediately be able to deduce the coin that Alice has still in her possession. Why? Because we are only using two coins with opposite values. We say in this case that we are dealing with two coherent coins since it is enough to know the value of one to deduce the value of the other. This is how information works nowadays. Don't you think that this is primitive...? It is! But why I said that it is possible to always get two opposite values when throwing two coins onto the ground? Well, the answer lies in quantum physics, in a concept called quantum entanglement.
In the article: "Probability theory in the FIFA World Cup Qualifiers," I outlined my wishes to write about quantum entanglement; however, I didn't know how to do it until that strange day when I heard from her again, when I hold her hands and understood that despite the distance there was a transparent and instantaneous bond that kept us always together... Right! Just like quantum physics! or better said, just like quantum entanglement. To understand this concept, let us consider the two coins again. If we can associate the current classical world of information with a two-dimensional system, then the quantum world will be associated with a three-dimensional system, keep in mind that the quantum world is more abstract than we think. In this new representation, the coins have a new degree of freedom and therefore they can be placed on a plane in a vertical position, see Fig. 4. In such a position, they can take both values at the same time. Keep in mind that we are now talking about quantum coins. While in the classical world each coin could only take one value, in the quantum world both values coexist on both sides of the coin, due to this we often speak of quantum-bits or better said "qubits". Quantum systems are governed by probability, because all values coexist and in order to choose one, a measurement has to be made; in the case of coins, let's say, you would have to throw them on the ground and see what values they take. This is the only way to define a state that can be understood by the human eye. But that's not all, quantum entanglement goes one step further and tells us that if we make this measurement with two coins that have the same quantum origin, it is enough to observe the value that one adopts, to know that the other coin will adopt the opposite value, no matter how far apart they are, as though there were a transparent and instantaneous bond that kept them always together. You could bet on this a million dollars and you won't lose a single game... While in the classical world your chances of getting two coins with opposite values is 2/4, in the quantum world it is 4/4. How does this influence the flow of information?
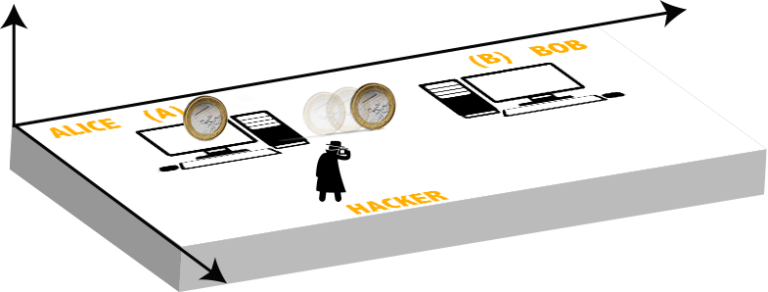
Let's go back to Alice and Bob's computers. In this case, computer A stores two coins subject to the laws of quantum entanglement. They have not yet been measured and therefore their values are not defined, that is, they are aligned vertically on the plane. Alice wants to convey some information to Bob. She has no choice but to send him one of the coins. At an intermediate point, the hacker may steal the information, but there is no such information because the coin is rolling on the plane with the two values on each side, see Fig. 4. In the classical world we saw that the coin that traveled from A to B already was defined, and therefore the information was already set. In the quantum world, this is not the case; therefore, the hacker has one option left and is to set himself that information, that is, to throw the coin onto the ground and check the value he obtains. Notice that in this case, the hacker is not stealing any information, he is just perturbing the coin that Alice sent. Let's say that he throws it and gets heads up. Being the coin subject to the laws of quantum entanglement, then the other coin that Alice has will necessarily be tails once she makes her measurement. As you can see, up to this point the hacker is the only one who knows the values of the coins, but these values have no meaning, because Alice didn't set them. For example, if Alice would like to give a meaning to the values, she could call Bob using a conventional telephone line and tell him that if he gets heads it means "YES" and if he gets tails it means "NO". But to do so, Alice must be sure that no one has altered the information. In this first example, let's assume that Alice doesn't know that there is hacker, then she will make her measurement thinking that all is fine and as expected she will get tails. Now, she is ready to make the phone call because she is sure that Bob will get heads. The hacker, on the other hand, will seek to go unnoticed, to do so, he will send to Bob the measured coin. Because this coin has already been defined, then it will travel on the plane like in the two-dimensional case, therefore when Bob makes his measurement, quantum entanglement no longer will apply. The hacker has succeeded with his plan. He has not been detected and knows the value of the coin that Alice has in her possession, as well as the value that she believes Bob has in his. All what is left for the hacker is to intercept the phone call to know the meaning of the values that Alice is about to share. With this example, it seems that quantum entanglement is not helpful to transfer information; however, the quantum world is more abstract than we think. In fact, quantum entanglement presents a special peculiarity: "For two particles to obtain opposite values, they must be measured in the same direction". For example, in the case of electrons, the measurement of the intrinsic angular momentum along the x, y, or z axes is considered, and this measurement can only take two values: spin-up and spin-down. Here we will use the coins instead to make it easy to digest, but bear in mind that the values heads and tails are related to the values spin-up and spin-down.
Considering that the measurement must be in the same direction to fulfill quantum entanglement, then this means that the above example is not completely true, the fact that the hacker measures heads does not necessarily imply that Alice will obtain tails, this will only happen if both measured the coins in the same direction. We can think in this case that "the same direction" is given by throwing them along the same axis, see Fig. 5.
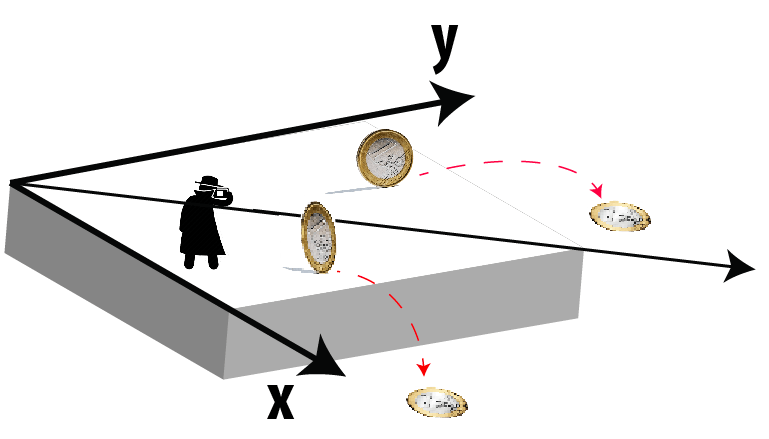
Let's see how this influences the flow of information. Initially we said that the hacker gets heads by making his measurement, now we will specify that he made it along the x-axis. The above example is correct only if Alice chooses the same axis as the hacker, but she is free to choose any axis that she wants. This is a random decision. Whether or not the axes coincide is a matter of luck. Let's say that Alice chooses another direction, then her coin has a chance of being heads as well. Only along the x-axis we will be convinced that Alice would get tails. As you can see, due to this peculiarity, the hacker cannot figure out the value of the coin Alice has. When she makes her measurement, you should also notice that in that moment both coins have been measured, this implies that the system has collapsed and therefore, quantum entanglement is not valid anymore, that is, any subsequent measurement taken in one coin will have no influence on the other. What is left for the hacker is to steal something from Bob's side. To go unnoticed, he will send to Bob the coin that he has measured, he will do it classically (two-dimensional case) because the coin is already on the plane. If Bob chooses the x-axis to measure the arriving coin (the same axis as the hacker), then the result will not be altered, Bob will measure heads. This is great for the hacker; however, unluckily for him, the situation is quite similar to Alice's side, if Bob chooses another axis, the coin has a chance of being heads or being tails... Let's say that fate plays a trick on the hacker and Bob picks the same axis Alice used, and by chance both get heads. At this point, the hacker does not know the value of the coins, he has lost every chance of stealing the information. Alice will communicate with Bob over the phone and ask him for the axis of his measurement and the value he obtained. With this, she will discover that there is someone who has altered the result because if both have used the same axis, then Bob should have measured tails if she got heads. As you can see in this analysis, with some luck the hacker may go unnoticed, but this luck seems to exist because we have used only two coins, imagine now that we take more than 100 pairs, all subject to quantum entanglement. The hacker to succeed needs a miracle to win 100 times in a row, or to put it in perspective, is like winning the lottery 100 consecutive times. Nobody has such a luck. The future is only one. The hacker cannot steal any information... and therefore companies like Avast won't be needed anymore.
To finalize, let us now consider the case where the hacker decides not to touch the information. Alice will do the respective tests to conclude that there are no intruders at the intermediate point. With that, she is ready to associate the real information to the coin. To do so, first she will use two coins subject to quantum entanglement. She will measure one along the x-axis and send the other to Bob. Bob is free to choose whatever axis he wants. For simplicity, let's assume that Bob chooses the same axis, if not, the experience is repeated until he does so. Then, Alice calls Bob on the phone and asks him for the axis he used in his measurement. That information is enough for Alice to deduce the value of Bob's coin, e.g., if Alice got tails, Bob will necessarily get heads, so she will say: "Bob, if you measured heads it means YES, if you measured tails it means NO." She won't mind if someone hears this information on the phone, because only she and Bob know the value of the coins. This is a simple way to understand quantum encryption based on quantum entanglement. A deeper explanation using the intrinsic angular momentum of the electron can be found in the scientific article published by Artur K. Ekert and entitled: "Quantum Cryptography Based on Bell's Theorem" (Physics Review Letters 67, 661).
To conclude, if we compare the results of the classical system (two-dimensional) and the quantum system (three-dimensional) we can see that in the end both are exactly the same. Alice and Bob end up having coins with opposite values, but don't be confused, the former is associated with today's machines and the latter with future quantum computers. It is true that current technology still does not allow quantum computers to be manufactured with the simplicity of the example given here, but we cannot underestimate human ingenuity since new concepts will necessarily emerge. Therefore, if the IoT era marks the boom of cybersecurity companies, with the quantum era they will lose popularity, they will be redefined and only those that innovate in the field of quantum physics will survive. It is a prediction of course, subject to the laws of probability.
Views: 1
Notifications
Receive the new articles in your email







