The blockchain
A summary of this section with some extra info appears in the following video:
I want you to think about video games, from Mario Bros to Mario Party, from Candy Crush to Angry Birds, from Pokemon Go to Fortnite. In these games we will always find items that will help us to complete the levels. Keep in mind that these are not the rewards, they are the items that will help us to obtain them. In the Bitcoin game, an item is the pair (m, f), that is, the data of a transfer. If there are many transfers, then there will be many items in the game. To understand this, let's make an analogy with Fortnite, a shooting game. In this game the items are the weapons and the ammunition, one collects them and stores them in a fictional bag, similarly, in the Bitcoin game each player collects pairs (m, f) and stores them in a fictional bag called a block. As you can see, in the Bitcoin game there are two types of players, those who generate transfers, or better say, the items of the game (passive players), and those who collect them (active players), the latter are called "miners." Let's focus on them because they are the most important. Keep in mind that there are many miners in the game, therefore each of them will have a block where they will store different (m, f) pairs. In Fig. 5 we represent this event, where the blocks generated by the players (miners) orbit around the public account. The question is, what block is transferred to the public account? Who would be the lucky miner? And more important, what happens with the other blocks? Think of Fortnite, two players with their respective weapons and ammunition, only one can win and in this game whoever kills the other wins, and if you have played Fortnite, or any other shooting game, you know that the items of your opponent return to the game once he is killed. In the Bitcoin game it is similar, the items go back to the game, so this information is not lost, but how is this achieved? In this case we are not talking about killing your opponent with a weapon, but rather a mathematical challenge is considered and whoever solves it first has the privilege to write his block in the public account. For the challenge, the Bitcoin game considers the SHA-256 cryptographic hash function, which is a function that transforms any given text (or any block) into a single, fixed-length value, the hash. For example, if we apply the SHA-256 hash function to the title of this article ("The origin of bitcoins. A complete explanation for beginners") we get:
But if we remove the "s" in bitcoins, i.e., "The origin of bitcoin. A complete explanation for beginners" and apply the function again, we get a completely different result:
As you can see, a slight change causes a great transformation. And why it is important? Let's say that Alice wants to send a digital document to Tom, she will first get the hash of the document and then send it. Upon receiving Tom the document, he will generate its own hash. If the hashes are identical, it means that no one has altered the information, not even by removing a single "s," but if the hash has changed, it means that a third party has modified it. Consequently, hashes are used to make sure that no one has altered the information, and that is why Satoshi implemented them in the Bitcoin game. To understand it better, let's focus on one block.
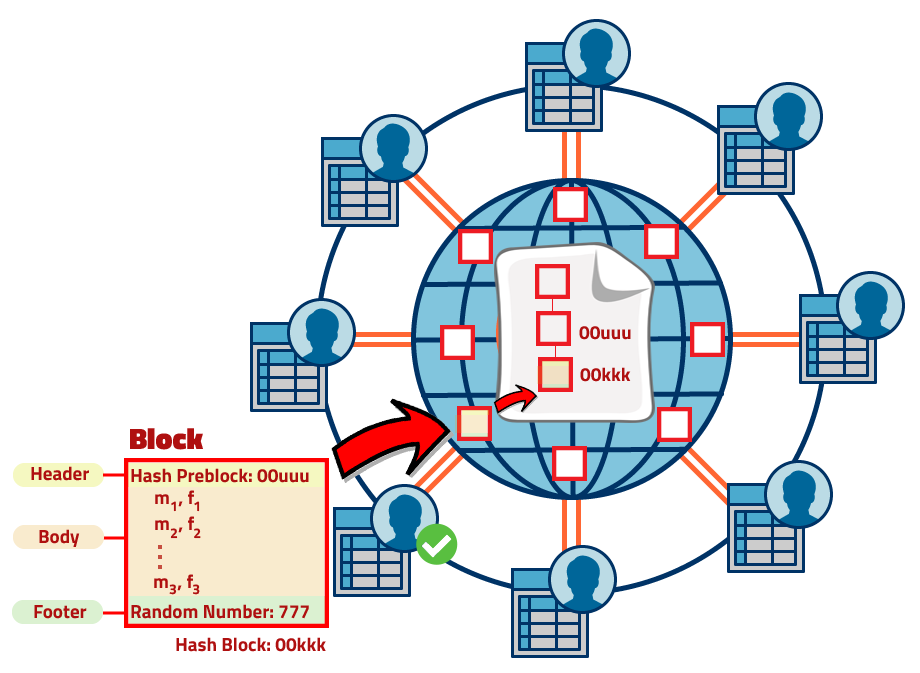
As you can see in Fig. 5, the red box represents a block and is made up of three parts: a header, a body and a footer, in the header is the hash of the previous block, in the body are all the transfers collected, and in the footer the player can write whatever he wants. What the player has to do to win is to define the hash of his block but under one condition: "This new hash must start with a fixed number of zeros." To achieve this, the player has to use the footer to find a random combination that meets the criteria of the hash. Curiously, getting it is very difficult, it is like throwing 10 dice together and try to get at least in 5 of them the value of 1. To achieve this one must have to repeat the experience countless times until getting the right result, it demands a lot of effort and at the same time there is luck. As I said, the player who generates the hash wins, but above all, the one who obtains the validation of the others. And what do the winner get? The reward of the Bitcoin game, that is, once your block is written on the public account, you are rewarded with bitcoin tokens, and as you can see in Fig. 5, this public account is a collection of winning blocks, in sequence, linked by the hashes in their respective headers and that is why it is usually referred to as the blockchain.
Up to this point you should keep in mind the following. The public account is the blockchain and it contains the history of all bitcoin transactions, so it is possible to know how many bitcoins each user has, we do not know exactly who these users are but that is irrelevant. Thanks to ECDSA encryption, bitcoin transfers are anonymous and protected from impersonation. What about the blockchain? Is it safe and immutable? To answer this, let's consider that Bob tries to change some data in a block that is already written in the public account. By doing so he will be altering the hash of that block, but also the hash of every subsequent block. Why? Because every block keeps the hash of the previous block in its header, creating a domino effect. In this sense if the hashes are changed, it is easy to realize that someone has altered the data. You may have doubts and say to yourself: "But if you delete some data and change the hash, it changes everything and we cannot go back in time. It's like having an important document on your desk and by mistake someone spills coffee on it, you will get crazy because this document is lost... You're right and that's why I waited up to here to tell you exactly how this public account really works. In Fig. 6 I show you two representations of the public account. The left one is a bit incorrect, the right one is how it actually is.
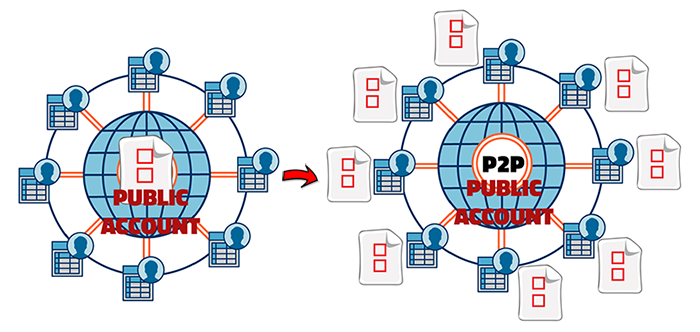
As you can see, in reality everyone has a copy of the public account, we already said that a peer to peer program allows transfers from PC to PC, therefore, in the universe of bitcoins, the public account is the one that is transferred, or rather, the blocks of the blockchain. Which block you will copy depends on how you filter the fake ones. For example, if Bob alters his copy of the public account, then he will change by default the hash of the block, and if you see that there are 10,000 users that have identical blocks and the hashes are totally different from Bob's, then you can intuitively guess that Bob has a fake information and you won't pay attention to him. For Bob to succeed he must control more than 50% of the miners' accounts, something that is likely impossible to happen because of the big quantity of players that Bitcoin has. For this reason, the transaction history is protected thanks to the concept of the blockchain.
Now let's move on to discuss two interesting scenarios in which Bob will attempt to corrupt the system. This will allow us to further understand the concept of the blockchain and its complete reliability.
1. Create a block with a fake transaction
We already know that Bob cannot alter the past of the public account because it is protected by the hashes. Now he will try to alter the future. For this, he will become a miner in order to win the game. He will collect (m, f) pairs and set his block; however, he will include a false transaction in it. He will proceed to obtain the hash and become the winning block, if he succeeds, in theory, his block would be written on the public account. Unfortunately for him, this will not be possible even if he solves the hash first, because the other players will have to validate his block, that is, verify the transactions in it using the special boolean function "v" that we described in the previous section. Moreover, every other player will check that the hash obtained is correct. In this particular example, the other players will certainly find out that Bob has made a mistake and therefore he won't be accepted as the winner of the game. As you can see, this is a consensus, it is not enough to be the first solving the hash, but it is also essential to obtain the validation of the other players, and the others will always seek to act correctly because there is a reward behind.
2. The double spending
In the second part of the article we said that ECDSA encryption prevents double spending spoofing, that is, Bob would not be able to replicate transactions made by other users; however, this encryption cannot prevent double spending without spoofing. Let me explain, Bob understands that false transactions will not get him anywhere, so he will seek to use true transactions. Let's say that Bob in his personal account "Z" has 10 BTC, that is, the transaction history (the public account) knows that account "Z" has 10 BTC to date. If Bob transfers those bitcoins to another account, the ECDSA encryption will validate it as correct. Bob will use this to his advantage and make the following transfers:
As you can see, Bob only has 10 BTC and he is using it twice to send to two different accounts, L and M. Keep in mind that this is possible because the transaction history does not yet have any new transfers recorded by Bob, so these pairs (m, f) will be sent to the public account as correct transactions validated by the ECDSA encryption; however, they will first orbit around the public account and it will be the miners who will add them to their corresponding blocks to verify them and obtain the hashes. Let us consider that two miners store each of the transfers in their blocks. Again, since the transaction history only records that "Z" has 10 BTC in his possession, then both transfers when verified by the miners will be correct; however, in each level of the game there is only one winner, and of those two miners who found the hashes of their respective blocks, only one can win, that is, one of the transfers, and only one, will be written in the blockchain... the other transaction will return to the game so that others can verify it and when this is the case it will no longer be valid because there will already be a new transfer made by "Z" in the history of the public account. What happens if both miners get their hashes at the same time and both are declared winners? In this case, you should remember Fig. 6 and keep in mind that the blockchain, or public account, only exists because everyone copies it to their PC, that is, the blockchain becomes valid once the majority has it on their PC. In the case of two miners creating two new blocks, then two blockchains will emerge. Some players will choose to copy the first miner's block and other players will choose to add the second miner's block, this is random and the game is not decided until a subsequent block is created, that is, of those 2 blockchains that have divided the game into two bands, only the one that will add a subsequent new winning block will succeed and emerge as the only blockchain. In simple words, whoever has the longest blockchain always wins because it involves a greater computational effort, and by consensus everyone will end up migrating to it. In this sense, the double spending is impossible, and in general, corrupting the Bitcoin system is unfeasible, of course, this could possibly change with the commercialization of quantum computers, which will be able to decrypt information in a short time and generate winning blocks with ease. However, when this era arrives, the protocols of bitcoins will change and it is very likely that we will start using quantum encryptions instead. If you want to know more about quantum cryptography, you can check the following article: "Quantum entanglement and the end of cybersecurity."
Finally, what can we say about the future? If someone manages to hack the blockchain, it is very likely that the price of bitcoins will drop to zero, that is, the hacker would not get any benefit from it. That is why hackers are not obsessed with this, rather they are interested in stealing bitcoins from exchanges, which are central entities that serve the purpose of exchanging bitcoins for dollars. If today you hear about bitcoin thefts on the internet, these have nothing to do with the blockchain, it is exclusive to third parties because hackers have already shown that they love Bitcoin and they will protect it implementing protocols. Therefore, the only ones who can destroy bitcoins in the future are the governments, but as long as this doesn't happen, the price of bitcoins will continue to grow. Because of this I own bitcoins and I'm not willing to sell them. Of course nothing is perfect, and the problem with Bitcoin is that it is creating a new generation of wealthy people, and these people will probably control the world in the future, giving rise to more inequalities. That's why today, here is an ideological war revolving around bitcoins. On one side we have the conservative millionaires like Bill Gates, Warren Buffett and Peter Schiff, who believe that bitcoin has no future. But on the other extreme we have the new minds of tomorrow like Jack Dorsey, Elon Musk and the Winklevoss brothers, who shout to the world that bitcoin would become the most valuable asset in the world. Who will be right? Only the future will give us the answer.
In this article I have shared with you the bitcoin origin, I have neither told you about its history nor about its future. If you want to know about them, I invite you to read the article: "The past and the future of bitcoins. A mathematical history." In it, I give you more reasons why I firmly believe in this digital currency.
Views: 1
Notifications
Receive the new articles in your email